SQL Injection Error Fixing
SQL Injection is a technique, where an attacker uses an unverified input in order to win over the application to run the SQL code that is suspected to manipulate database. This practice is basically done for attacking SQL database driven websites.
In short, we can call it as a procedure where the vicious data is entered to the input fields which processed by backend Server (like ORACLE, SQL Server) and returns back an unanticipated result against standard development of the application. Such type of attacks are commonly done in login screens.
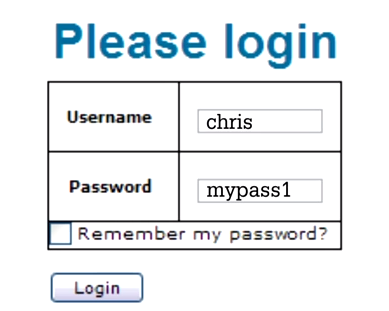
Example:
The user name and password strings are saved in SQL statement which looks like this:

With this statement, the application is asking if any legitimate account with this username and password exists. (According to SQL syntax, any text provided by the user should be saved in single quotes. Meanwhile, note that this single quote is a part of SQL syntax and not the user's input). Escape characters (like single quotes) are special characters and if the hacker is able to smuggle them, then it is possible for him to change SQL queries, logic, even behavior of the application.
The first thing that SQL injection attacker will do is find out if the site is using SQL database by entering single quote in the username and password field.
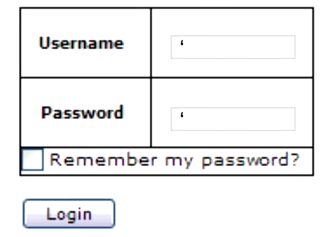
Single quotes are special characters in SQL language and using them as username and password end up with an error in the website and this error can help the attacker to confirm that the website is using SQL database.

Now the real SQL injection begins. The attacker can enter following comment logic.
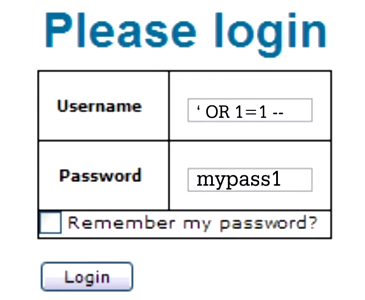
The comment will lead to a valid user name as the value 1=1 is always true.

This way, the attacker can login to the credential of first user in the table. The range of data manipulation can lead to data retrieval to complete table deletion to database corruption (due to statement changes).
Word of Caution: Make sure that you do necessary string checking for special SQL characters. Moreover, there are software applications that can check entire website against injection.
How to Work Around: Now, the important factor is how to deal with consequences of SQL injection practice, especially when statements manipulation causes database corruption or any table from the database is deleted. To handle the scenario, SQL repair utility can be adopted.
Following are the reasons why?
- If the primary (.mdf) or secondary (.ndf) system database files are corrupt, the software will help recovering data from it.
- If the tables are deleted from database, software will allow restoring them when Advance Scan mode is selected.
Database corruption caused by SQL injection errors can be fixed using the software. To try out the solution for its quality check, free demo version can be downloaded that gives a preview of recovered data. To export database to SQL compatible scripts or to live SQL Server, licensed version of the tool should be purchased.
